Magnetometer is a less known sensor. It equips web browsers with the ability to read the magnetic field strength using the built-in magnetometer device sensors and the W3C Magnetometer API. It might be useful in some specific use cases such as peripheral devices (like a gamepad, to control the user’s gestures) or to… make a web app demonstrating how a compass works, and so on. It can also aid in indoor navigation.
As should be clear by today, even the sensors or features not seen as providing sensitive data in practice often may bring privacy consequences, enabling data leaks, fingerprinting, or location tracking. Web browsers on mobile devices are powerful, offering access to many advanced features. Previously I analyzed the privacy of a bunch of various web browser features (e.g. vibration, proximity, web Bluetooth, light sensor, and such).
Magnetometer, how does it work
The actual use is quite simple.
let sensor = new Magnetometer();
sensor.start();
sensor.onreading = () => {
let t = sensor.timestamp;
let x = sensor.x; let y = sensor.y; let z = sensor.z;
let M = Math.sqrt(Math.pow(x,2) + Math.pow(y,2) + Math.pow(z,2));The code is all that’s needed to access the magnetic field around device axes (x, y, z) and also the computed magnitude of the magnetic field (a mockup demo is here). It’s also already implemented in the latest Chrome browser (behind a flag; to enable, visit chrome://flags/#enable-generic-sensor-extra-classes).
This post is about security and privacy so what may be the potential issues? I provide a survey below.
Assessment
Magnetometers are sensitive sensors, potentially able to detect the presence of nearby objects and even extracting their fingerprints. They also may or may not allow some rather unorthodox things.
Pairing and covert communication.
The magnetometer can be used to pair two devices in close proximity. Analytically this may be as simple as having one’s device near to another for a short time. That’s all that’s needed to extract a device fingerprint. Such uses of pairing work in practice, and can be used in interesting ways. Can it be turned against the user is another story. Magnetic fields could also be used as an out-of-band communication channel. It can establish a covert communication channel.
Offline user tracking and location tracking
The magnetometer can be used to tracking smartphones in a beacon-like scheme and application/aid assisting in uses/abuses to track the location (with 10 meters accuracy), as well as to discover the co-location proximity information (contact tracing). The sensor can also be fused with other sensors like the light sensor to locate the user indoor, while indoor position tracking may take advantage over unique in-building magnetic fingerprints (software to do this exists), or maybe even tracking the location beyond.
Leaks of web browsing history?
Due to how modern mobile hardware is built and works, magnetic field readings may even allow the discovery of what the user is doing: which application is in use, or even which website the user is visiting (so web browsing history leak). This may be made possible by establishing the fingerprints of various apps in use, or the fingerprint of the visited websites - based on the disturbances in the magnetic field caused by the changes in the CPU, for example by the high workload caused by device use. The image below shows example correlations:
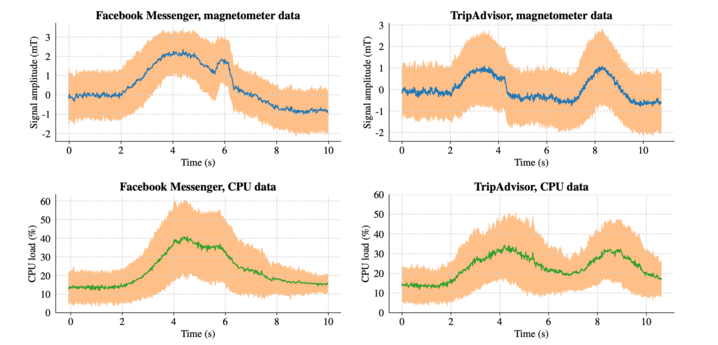
That would mean that using the Magnetometer may allow the exfiltration of information across sites (assuming it could be done in practice)
Beacons/tracking gates?
Some cases of uses/abuses would require specialized infrastructure. Imagine beacons at the store. Or gates on motorways, which could be used to track and monitor the behavior of drivers:
“when smartphones are placed on the driver side of a vehicle, the EMF measurements are statistically larger than those collected on the passenger side … The reason behind this is that the driver’s position is closer to more electronically charged components in most vehicles (e.g., engines, airbags, fuse boxes)”,
meaning that infrastructure could potentially detect which smartphone user is the driver?
Risks
Among the specific risks are the following
Location tracking. Magnetometer may aid in detection of user’s movement and location, especially when fused with other sensors
Profiling risk stems from potential analyses of patterns of changes. In principle, a magnetometer could be used to detect the presence objects but in my view, it is unlikely to detect what particular object are nearby. When it comes to the patterns of using a device, it seems the reading of magnetometer may be correlated with other hardware like the CPU, which may sometimes reveal information such as the used app or the visited website. How stable it is, is another story.
What can be done about it?
Web browser Permissions. This sensor should be gated with browser permissions. If I understand correctly, this is how it’s recommended in the current specification.
Frequency cap? Currently, the Magnetometer as implemented in web browsers could provide a substantial frequency of the sensor readout (60 Hz?). One potential mitigation strategy would be to cap the frequency, for example at 1 Hz. If concerned with potential abuses (while this may not rule out them all).
Precision cap? Currently, the precision the readout values is substantial. If it’s possible to decrease it without compromising realistic use cases, this should be done.
If the W3C Magnetometer is to work following explicit user permission (following a user prompt), some of the risks are mitigated. However, it’s important to note that a website with access to the magnetometer sensor would of course still be able to use the sensor.
Summary
Privacy design, analysis and standards are always fascinating. Including their practical use or abuse cases. Analysing these is not always straightforward. Sometimes - time consuming. Depending on the goal, many approaches are possible.
I wanted to write an analysis devoted to this sensor for some time now. So here it is!
Did you like the assessment and analysis? Any questions, comments, complaints or offers? Feel free to reach out: me@lukaszolejnik.com